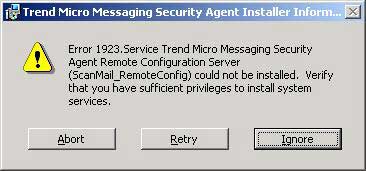
 This week I upgraded the Trend Micro SMB installation on my “dog food” server to version 3.6. It kind of worked. The virus checking stuff upgraded nicely but the Messaging Security portion did not. I got this message, “Error 1923.Service Trend Micro Messaging Security Agent Remote Configuration Server(ScanMail_RemoteConfig) could not be installed”.
This week I upgraded the Trend Micro SMB installation on my “dog food” server to version 3.6. It kind of worked. The virus checking stuff upgraded nicely but the Messaging Security portion did not. I got this message, “Error 1923.Service Trend Micro Messaging Security Agent Remote Configuration Server(ScanMail_RemoteConfig) could not be installed”.
I researched the problem and it said I should check my privileges. After researching what privileges it was complaining about, I figured out that the privileges for the Administrator userid were just fine. So I rebooted and tried to install Messaging Security portion again. I was unsuccessful but this time it told me to install it from the Security Dashboard. I don’t remember seeing that message before but I was game. After a little research I found these instructions on how do this.
Installing the Messaging Security Agent from the Security Dashboard
These instructions were a little too short for me since the installation process asked me a few more questions than were included in the instructions. The installation process asked me which directory to install Messaging Security in and the “shared” directory. I was not sure what they wanted for the shared directory since this field was prefilled with C$. C$ looks like a “share” to me and I was clueless about a shared directory. If Trend Micro has a shared directory they want me to use, they hid it well. Since I was installing these files on my “H” drive, I assumed they wanted the “share” for the drive, H$. Anyway that is what I gave it. When I pressed the enter key, a screen showing the installation status popped up. The status screen updated several times over the next ten minutes before it finally completed. Now when I check the “Live Status” and “Security Settings” screens they show me that the Anti-spam is working. Since Microsoft’s Intelligent Messaging Filter catches most of the spam for my “dog food” server I got through this unscathed.

